Just before the holidays I had a problem with a 802.11 Wi-Fi Ethernet radios I was working on. I had a pair of wireless radios connecting a PC to an office network. Something coming in on the radios caused severe interruptions to our network, including taking out a VoIP telephone system used for customer service.
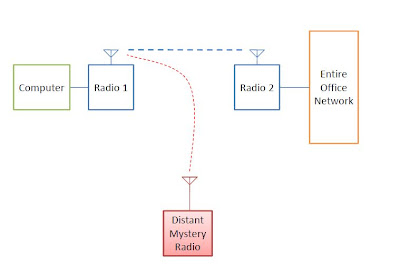
A wireless sniff showed a weak signal connecting to my pair of radios under test. That means they must have intentionally selected my test network by selecting the same SSID (network name). When we looked deeper, it appeared that the offending signal was rapidly changing IP address to addresses used by various equipment on the office network. It had to be a hacker. The signal was weak, probably not in the immediate area. Maybe it was someone from the glacial hills a mile north of the office, I thought as I looked out the window at the hundreds of snow-coverd roofs in the distance. Were they just sitting there, in front of a computer with a small 2.4GHz antenna on their roof or in their attic, messing with me? Or did the have an automated script running that hacked into networks and logged its activity for later review?
I immediately turned on encryption on my test radios. I used an advanced encryption setting because the older WEP encryption can be easily defeated. The hacker couldn’t get in anymore. I tried turning off encryption, and he came right back.
A colleague eventually found the source of the problem: it was another unrelated product I have been working on only a few meters away from the two radios under test.

The signal appeared weak because this unrelated product had no antenna connected. A unfortunate “feature” of the product is that when not directed to connect to a specific network, it would connect to the first un-encrypted network it found. The product includes a module that is designed to be a client and take the address of a single device attached to it. A problem in the product caused it to attempt this on a port connected to an entire network. As a result it kept taking the address of the last thing it heard. Since it was connected to the office network and my wireless network, which was also connected to the office network, a loop was created.
I wonder how many times I spend more than a few hours on the wrong track. I had such a specific image of a person intentionally interfering with the network. I didn’t want to hear that I was indirectly responsible for the problem. It’s a reminder to avoid hasty conclusions and other pitfalls to critical thinking and to stay open to undesirable possibilities.


No comments:
Post a Comment